Create GitHub Secret
This guide demonstrates how to implement a self-service action in Port that allows you to create GitHub Secrets in your GitHub repository directly from Port.
In this example we are using a pre-defined GitHub Action from GitHub Marketplace called Create GitHub Secret Action.
Common use cases
- CI/CD Management: Store API keys, deployment tokens, and other credentials needed for automated workflows.
- Environment Configuration: Manage environment-specific secrets for different deployment stages.
- Security Compliance: Centralize secret creation with proper approval workflows and audit trails.
- Developer Productivity: Enable developers to create secrets without requiring direct repository access.
Prerequisites
- Complete the onboarding process.
- Port's GitHub app needs to be installed in your GitHub organization.
- A Classic Personal Access Token with the following scopes:
repo(Full control of private repositories).admin:org(Full control of orgs and teams, read and write org projects).
- Port Client ID and Client Secret (learn more).
Set up data model
To represent GitHub secrets in your Port catalog, we'll create a dedicated blueprint.
Create the GitHub Secret blueprint
-
Go to the Builder page of your portal.
-
Click on
+ Blueprint. -
Click on the
{...}button in the top right corner, and chooseEdit JSON. -
Add this JSON schema:
Blueprint flexibilityKeep in mind this can be any blueprint you would like and this is just an example. You can customize the properties based on your organization's needs.
GitHub Secret blueprint (Click to expand)
{
"identifier": "githubsecret",
"title": "GitHubSecret",
"icon": "Github",
"schema": {
"properties": {
"secret_key": {
"icon": "Github",
"title": "Secret Key",
"type": "string",
"description": "All Uppercase",
"pattern": "[^a-z]*$"
},
"secret_value": {
"icon": "Github",
"title": "Secret Value",
"type": "string"
}
},
"required": ["secret_key", "secret_value"]
},
"mirrorProperties": {},
"calculationProperties": {},
"relations": {}
} -
Click
Saveto create the blueprint.
Implementation
Add GitHub secrets
In your GitHub repository, go to Settings > Secrets and add the following secrets:
-
PERSONAL_ACCESS_TOKEN- A Classic Personal Access Token with the following scopes: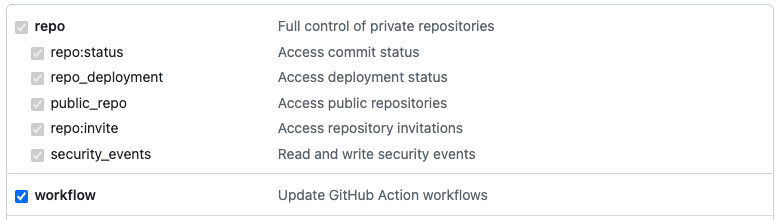
-
PORT_CLIENT_ID- Port Client ID learn more. -
PORT_CLIENT_SECRET- Port Client Secret learn more.
Add GitHub workflow
Create the file .github/workflows/create-repo-secret.yml in the .github/workflows folder of your repository.
We recommend creating a dedicated repository for the workflows that are used by Port actions.
Create GitHub Secret Workflow (Click to expand)
name: Create Repository Secret
on:
workflow_dispatch:
inputs:
secret_key:
type: string
description: Name of the secret's key
secret_value:
type: string
description: value of the secret
port_context:
required: false
description:
Who triggered the action and general context (blueprint, run id, etc...)
type: string
jobs:
create_secret:
runs-on: ubuntu-latest
steps:
- name: Mask secret value
run: echo "::add-mask::${{ inputs.secret_value }}"
- uses: gliech/create-github-secret-action@v1
with:
name: ${{ inputs.secret_key }}
value: ${{ inputs.secret_value }}
pa_token: ${{ secrets.PERSONAL_ACCESS_TOKEN }}
- name: Mask secret key
run: echo "::add-mask::${{ inputs.secret_key }}"
- name: UPSERT Entity
uses: port-labs/port-github-action@v1
with:
identifier: ${{ inputs.secret_key }}
title: ${{ inputs.secret_key }}
team: "[]"
icon: DefaultBlueprint
blueprint: ${{ fromJson(inputs.port_context).blueprint }}
properties: |-
{
"secret_key": "${{ inputs.secret_key }}",
"secret_value": "${{ inputs.secret_value }}"
}
relations: "{}"
clientId: ${{ secrets.PORT_CLIENT_ID }}
clientSecret: ${{ secrets.PORT_CLIENT_SECRET }}
baseUrl: https://api.getport.io
operation: UPSERT
runId: ${{ fromJson(inputs.port_context).runId }}
- name: Inform completion of request to create secret in Port
uses: port-labs/port-github-action@v1
with:
clientId: ${{ secrets.PORT_CLIENT_ID }}
clientSecret: ${{ secrets.PORT_CLIENT_SECRET }}
baseUrl: https://api.getport.io
operation: PATCH_RUN
status: "SUCCESS"
runId: ${{fromJson(inputs.port_context).runId}}
logMessage: "Created github secret ${{ github.event.inputs.secret_key }}"
Set up self-service action
Now we'll create a self-service action that allows users to create GitHub secrets through Port's interface.
-
Head to the self-service page.
-
Click on the
+ New Actionbutton. -
Click on the
{...} Edit JSONbutton. -
Copy and paste the following JSON configuration into the editor.
Create GitHub Secret Action (Click to expand)
Modification RequiredMake sure to replace
<GITHUB_ORG>and<GITHUB_REPO>with your GitHub organization and repository names respectively.{
"identifier": "create_git_hub_secret",
"title": "Create GitHub Secret",
"icon": "Github",
"description": "Creates a GitHub secret in my repository",
"trigger": {
"type": "self-service",
"operation": "CREATE",
"userInputs": {
"properties": {
"secret_key": {
"icon": "DefaultProperty",
"title": "Secret Key",
"type": "string",
"pattern": "^[^a-z]*$"
},
"secret_value": {
"icon": "DefaultProperty",
"title": "Secret Value",
"type": "string",
"encryption": "aes256-gcm"
}
},
"required": [
"secret_key",
"secret_value"
],
"order": [
"secret_key",
"secret_value"
]
},
"blueprintIdentifier": "githubsecret"
},
"invocationMethod": {
"type": "GITHUB",
"org": "<GITHUB_ORG_NAME>",
"repo": "<GITHUB_REPO_NAME>",
"workflow": "create-repo-secret.yml",
"workflowInputs": {
"secret_key": "{{ .inputs.\"secret_key\" }}",
"secret_value": "{{ .inputs.\"secret_value\" }}",
"port_context": {
"entity": "{{.entity}}",
"blueprint": "{{.action.blueprint}}",
"runId": "{{.run.id}}",
"trigger": "{{ .trigger }}"
}
},
"reportWorkflowStatus": true
},
"requiredApproval": false
} -
Click
Save.
Now you should see the Create GitHub Secret action in the self-service page. 🎉
Let's test it!
-
Head to the self-service page of your portal.
-
Click on the
Create GitHub Secretaction. -
Fill in the secret details:
- Secret Key: Enter a name for your secret (all uppercase, e.g.,
MY_API_KEY). - Secret Value: Enter the secret value (this will be encrypted).
- Secret Key: Enter a name for your secret (all uppercase, e.g.,
-
Click on
Execute. -
Wait for the workflow to complete.
-
Verify the secret was created:
- Check your GitHub repository's secrets in Settings > Secrets and variables > Actions.
- Verify the new entity appears in your Port catalog under the GitHub Secret blueprint.
You may want to restrict this action to specific users or teams. To do this:
- Edit the action by hovering over it and clicking on the
...button, then selectingEdit. - In the
Permissionstab, select the users or teams who can execute the action.